story about security E1: public key ↔ secret key, encrypt ↔ decrypt
One day
(keep scrolling)
.
.
.
.
.
.
Alice stayed at home for a long time and got bored.
.
.
.
.
.
.
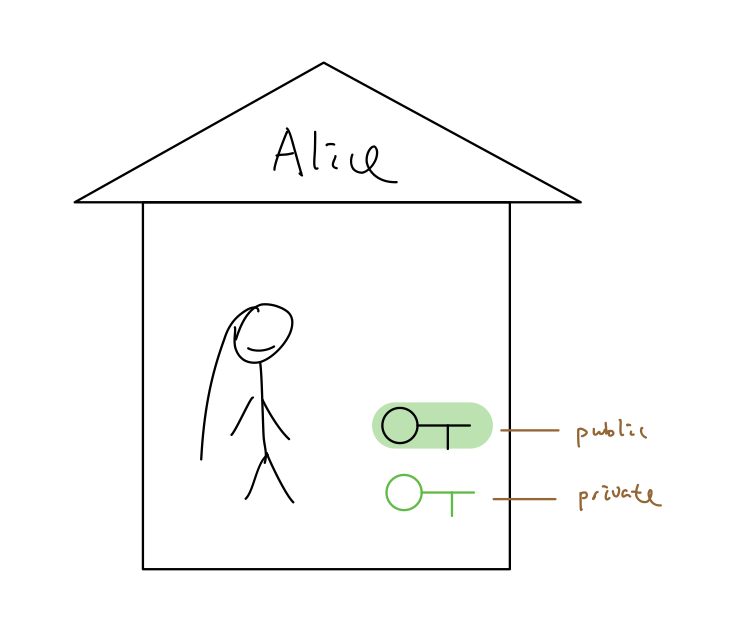
Alice generated a pair of keys (public key and private key). Alice was less bored.
.
.
.
.
.
.

One day, Alice encountred Bob. Through each other’s eyes, they knew they feel same inside.
.
.
.
.
.
.
.
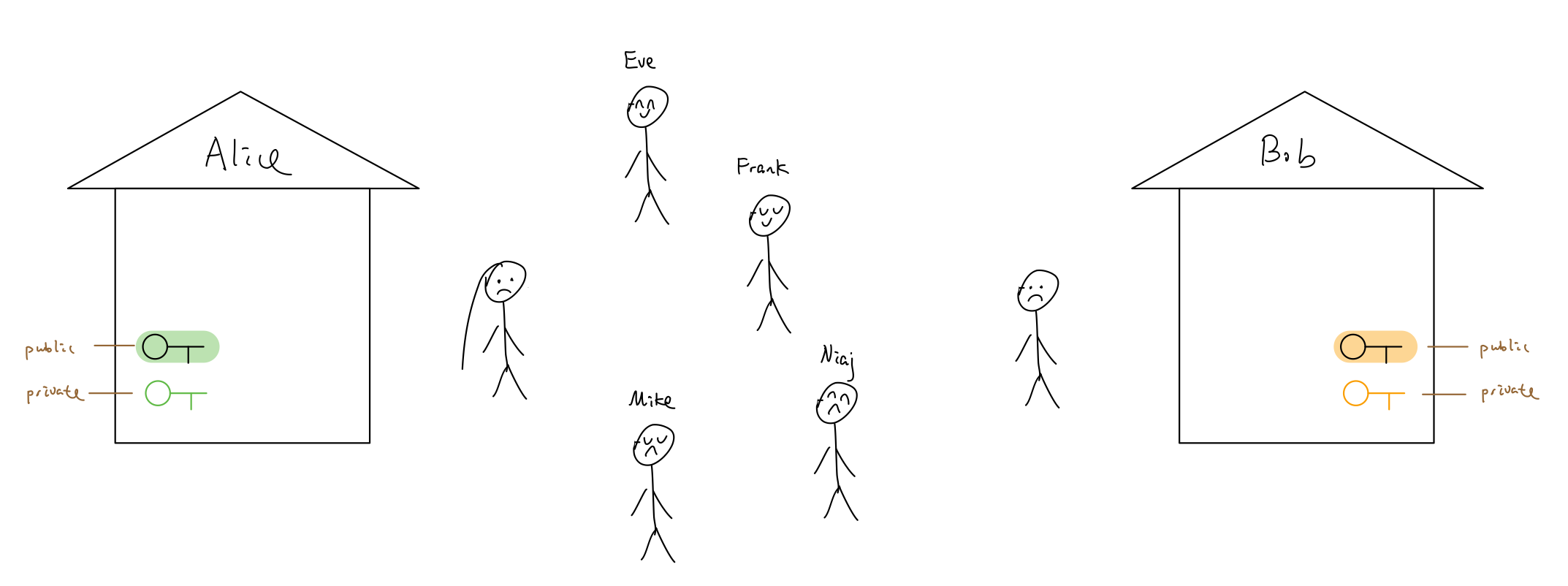
However, there were so many people around Alice and Bob. They could not chat freely, all they wanted was just to enjoy the time between them. But it was hard. After staring each other for a while, Alice and Bob both seemed to remember something and they went home.
.
.
.
.
.
.
.
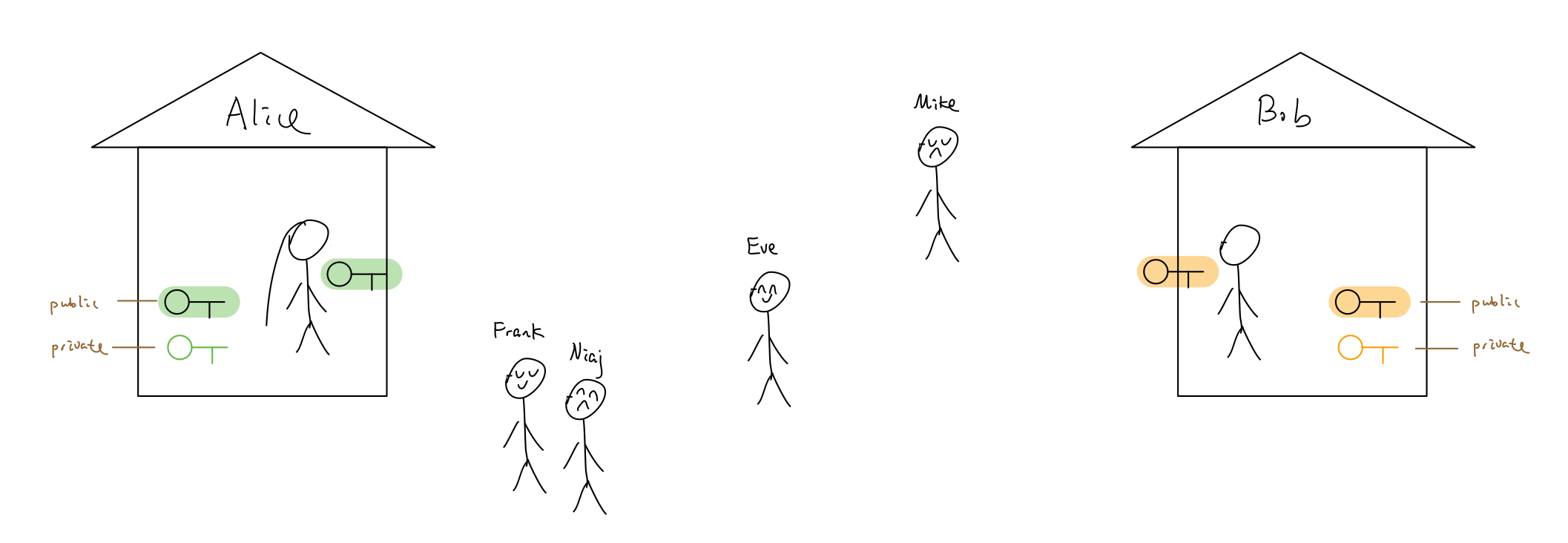
They went home, grabbed a copy of the their public key.
.
.
.
.
.
.
.
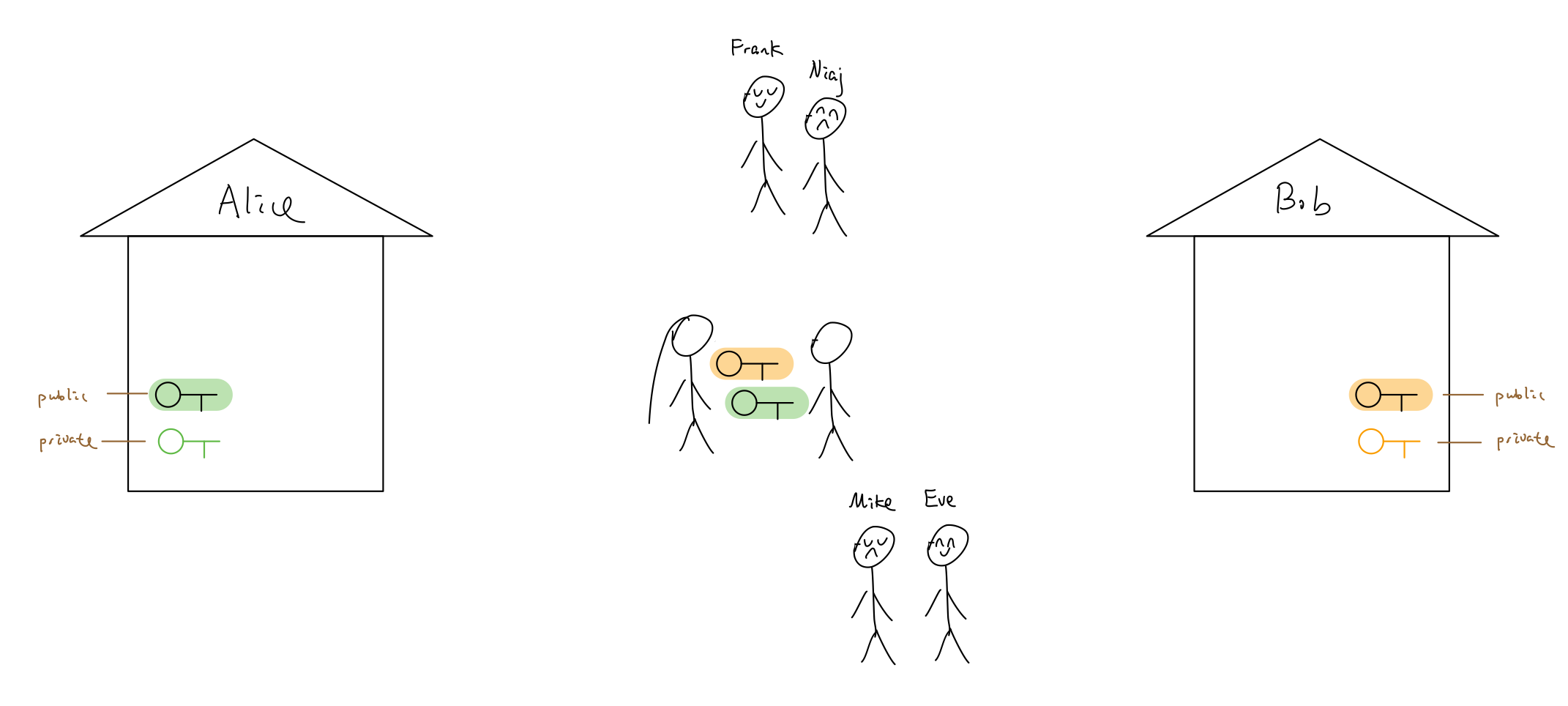
Alice: “Yo, wanna switch keys ?”
Bob: “Sure !!”
.
.
.
.
.
.
.
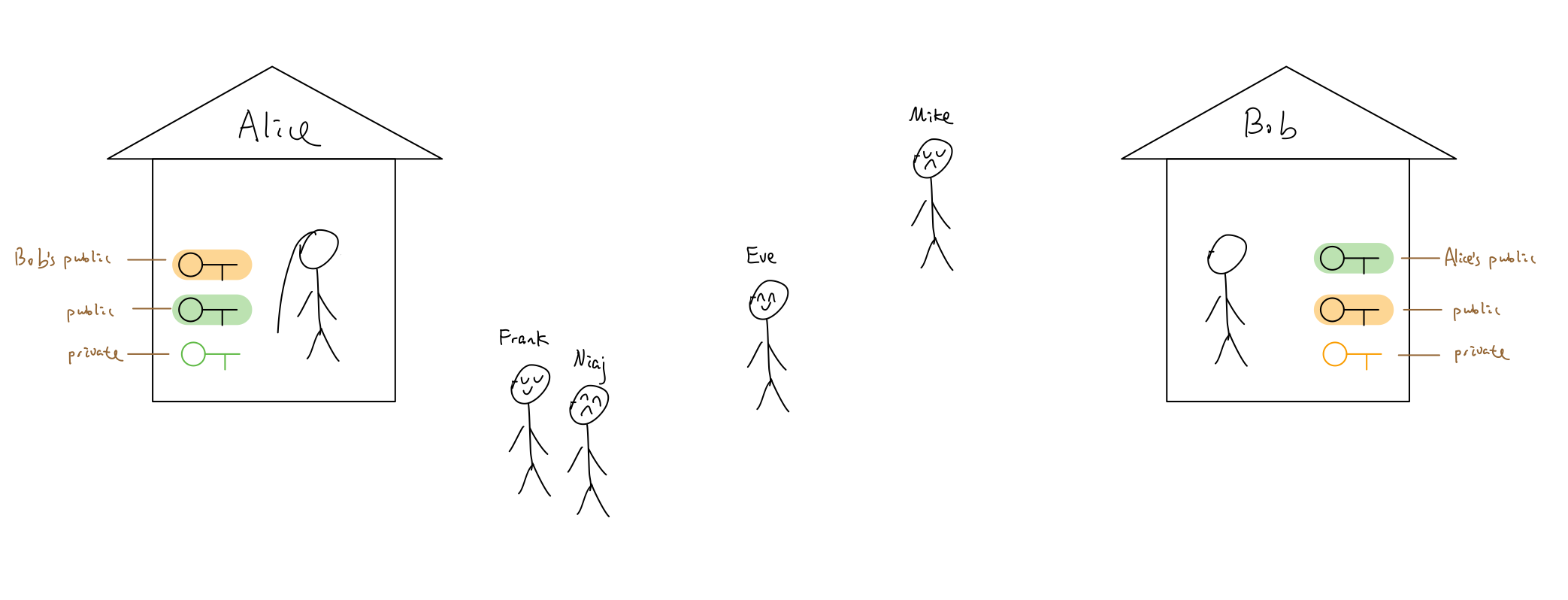
They brought the copy of each other’s public key home. Now Alice has Bob’s public key. Bob has Alice’s public key.
.
.
.
.
.
.
.
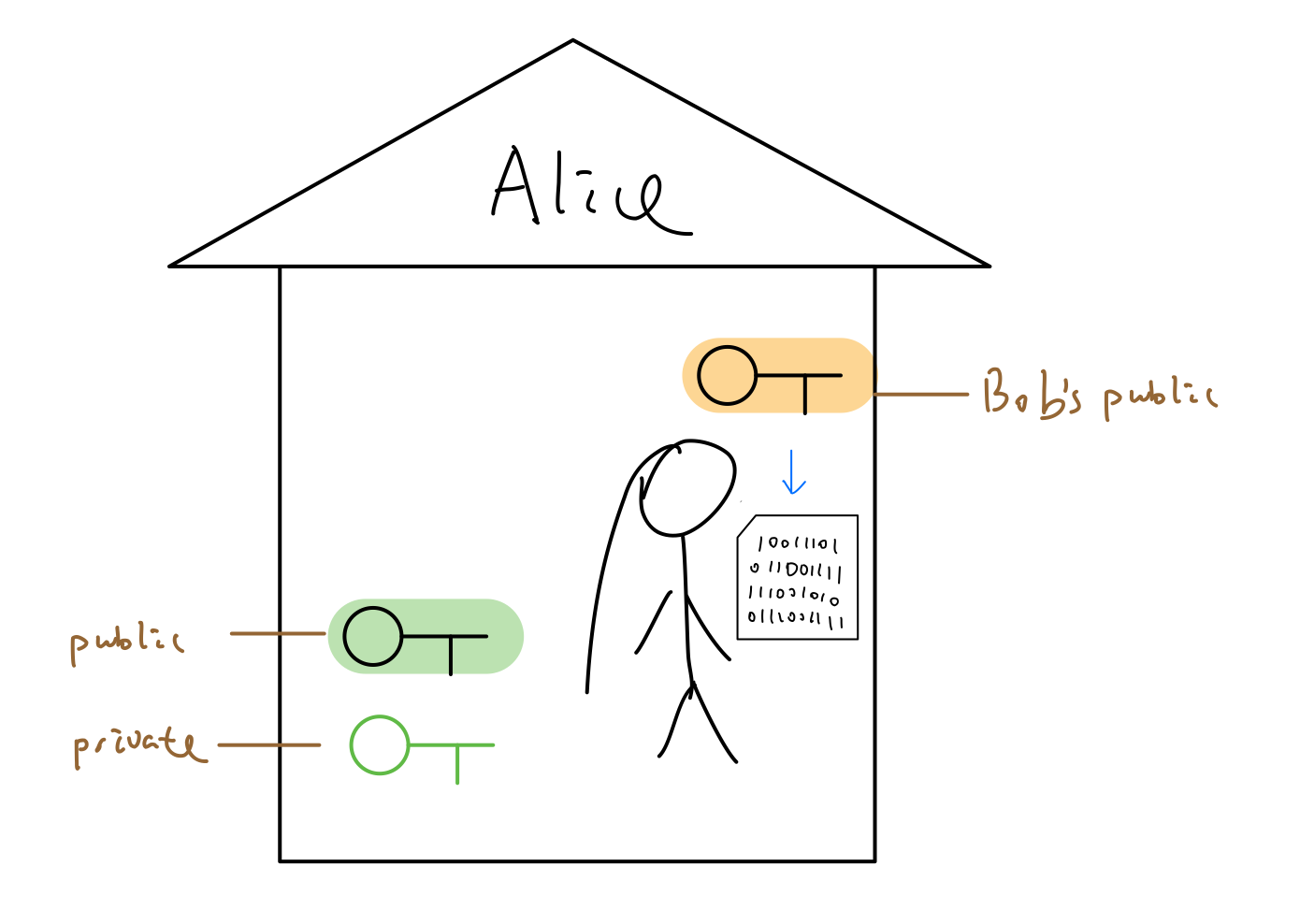
Alice wrote something using Bob’s public key. It turned out to be non-human-readable. What did she write ?
Alice knew that only Bob could understand what she wrote because Bob has the other pair of the key (private key).
.
.
.
.
.
.
.
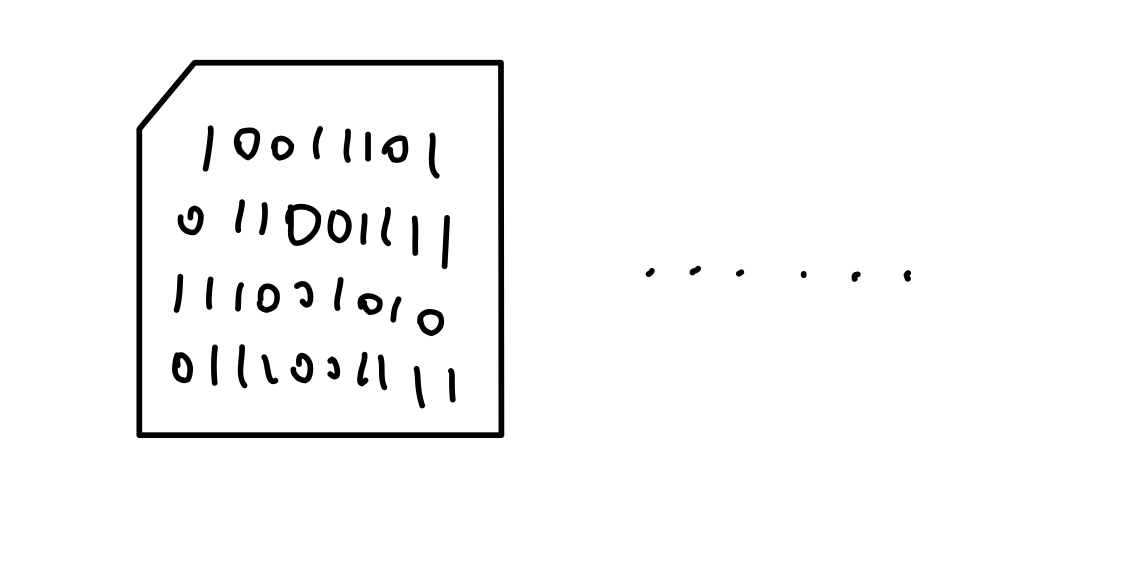
The non-human-readable message was being deliverred. It might take a while.
.
.
.
.
.
.
.
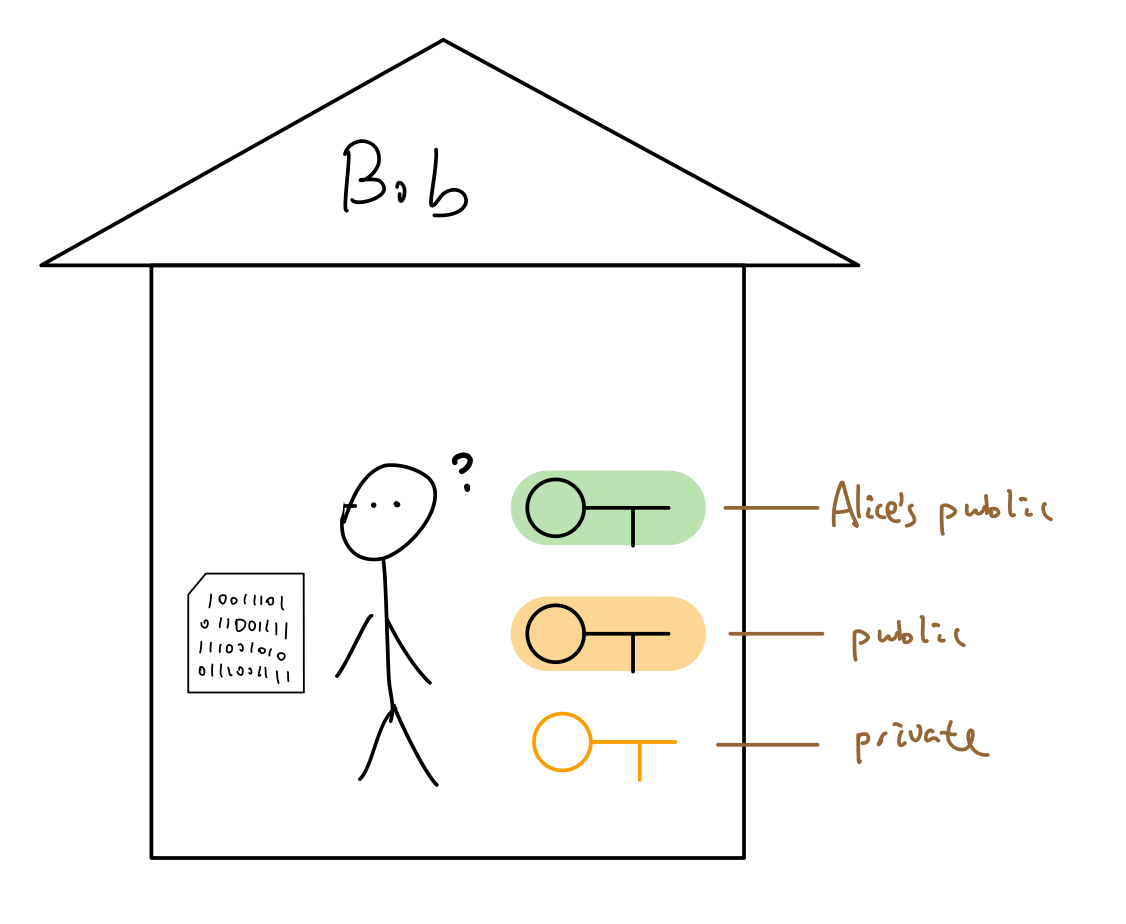
Bob: “What is this non-human-readable message?”
.
.
.
.
.
.
.
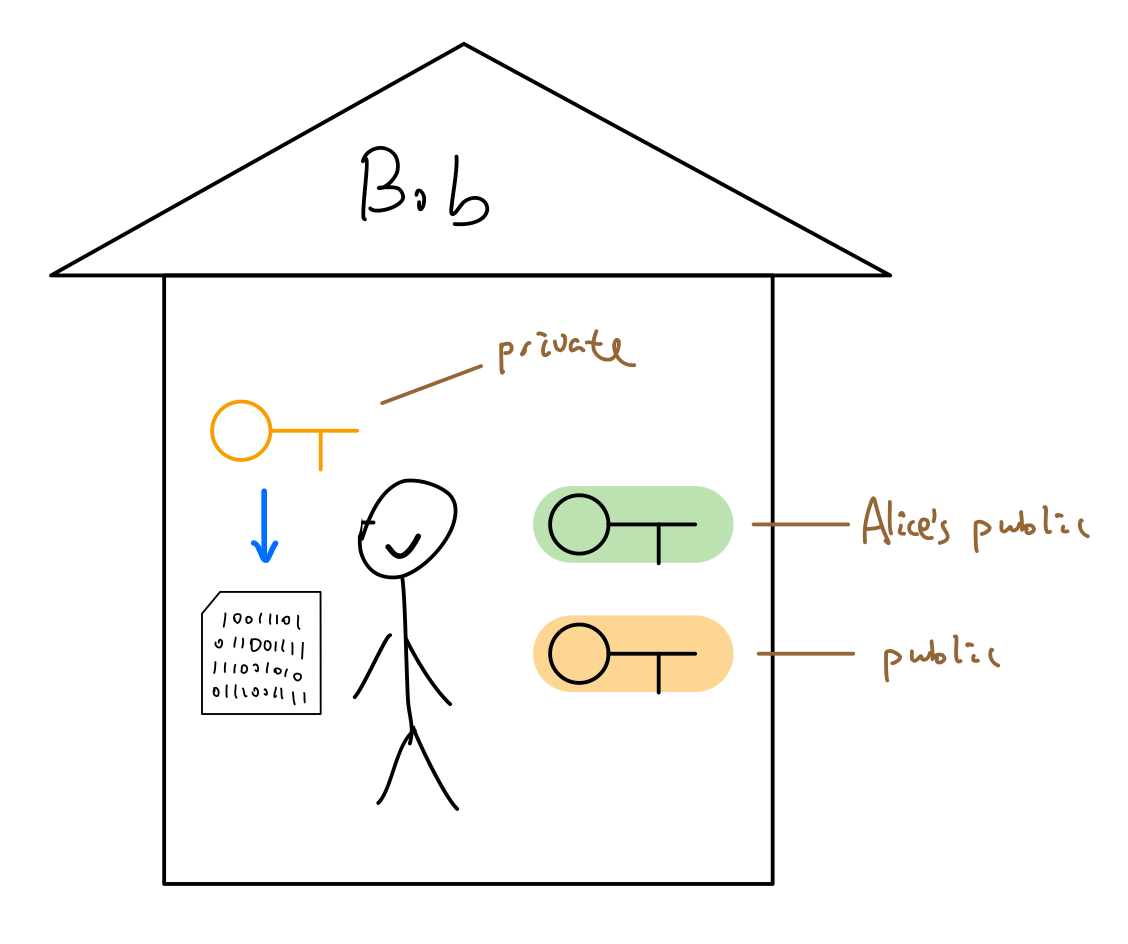
Bob realized that he has the private key so he could decrypte the message.
.
.
.
.
.
.
.

.
.
.
.
.
.
.

.
.
.
.
.
.
.
But how was Bob sure that the message was from Alice ?
The Alice Bob knew was not like that. (well, they only met once)
It was possible that someone tampered the message.
That must be it!
What indeed happened ?
.
.
.
.
next episode(incoming): “story about security E2: sign ↔ verify”
Author Alex Lai
LastMod 2020-04-08 (fadaa5a)